In the world of rapid application development, modern backends like Supabase and Firebase empower teams to build and ship at unprecedented speeds. This velocity, however, introduces a new set of critical security challenges. A simple misconfiguration in your Row Level Security (RLS) policies, a leaked service key embedded in a mobile app bundle, or an unprotected Remote Procedure Call (RPC) can expose your entire user database, leading to catastrophic data breaches. Generic advice simply won't suffice when the stakes are this high.
This guide provides a prioritised, actionable roundup of the top 10 api security best practices, tailored specifically for the nuances of Supabase, Firebase, and demanding mobile-backend workflows. We will move beyond abstract theory, offering concrete code snippets, practical implementation details, and automated checks you can integrate into your CI/CD pipeline immediately. Forget surface-level tips; this article is designed to be a comprehensive security playbook.
Here, you will learn how to properly implement and harden everything from authentication patterns and RLS policies to secrets management and rate limiting. The goal is to provide you with the specific knowledge needed to transform your application's security posture from vulnerable to resilient. By following these best practices, you can ensure you ship with confidence, protecting your users' data and your company's reputation without sacrificing development speed.
1. Implement Row Level Security (RLS) with Proper Authorization Rules
Row Level Security (RLS) is a powerful database feature that enforces data access restrictions at the database row level. Rather than managing access logic within your application code, RLS moves authorisation directly into the database, creating policies that filter which rows users can view, update, or delete based on their authenticated identity and claims. This is a cornerstone of modern api security best practices, particularly for platforms like Supabase that are built on PostgreSQL.
By default, tables are often unprotected. The fundamental principle of RLS is to enable it on all tables containing sensitive data and apply a "deny-by-default" stance. This means no one can access any data unless a specific policy explicitly grants them permission. This approach dramatically reduces the risk of accidental data leaks, a common vulnerability in multi-tenant applications.
Practical Implementation and Use Cases
A classic example is a SaaS platform where you must isolate tenant data. An RLS policy can ensure that an authenticated user can only access records where the organisation_id column matches their own organisation ID stored in their JWT claim.
- Healthcare Apps: Ensure patients can only view their own medical records by matching
auth.uid()with apatient_idcolumn. - Fintech Platforms: Isolate customer financial data by enforcing that a user's
organisation_idclaim matches the corresponding column in the transactions table. - Project Management Tools: Restrict team members to seeing only the tasks and projects associated with their assigned
workspace_id.
Actionable Tips for Hardening RLS
To effectively implement RLS, it's crucial to go beyond simple checks.
- Test Policies Rigorously: Use a variety of user roles and JWT claims to test for edge cases and potential logic flaws that could lead to data exposure.
- Automate RLS Scanning: Integrate tools like AuditYour.App into your CI/CD pipeline. Its RLS fuzzing capabilities can automatically discover subtle leakage vulnerabilities that manual testing might miss.
- Document and Audit: Maintain clear documentation for which policies protect which data columns and implement audit logging for any changes to your RLS rules.
For a deeper dive into crafting secure and efficient policies, explore this complete guide to Supabase RLS, which covers advanced patterns and common pitfalls.
2. Protect API Keys and Use Public/Anon Keys with Row Level Security
A critical, yet often overlooked, aspect of security involves the correct management of API keys. A foundational rule is that service-level or admin-level keys must never be exposed in client-side code, such as frontend web applications or mobile app bundles. These powerful keys grant extensive permissions and, if leaked, can lead to catastrophic data breaches. The correct approach is to use public (or anonymous) keys on the client-side, which are intentionally limited in scope and designed to work in tandem with robust authorisation rules.
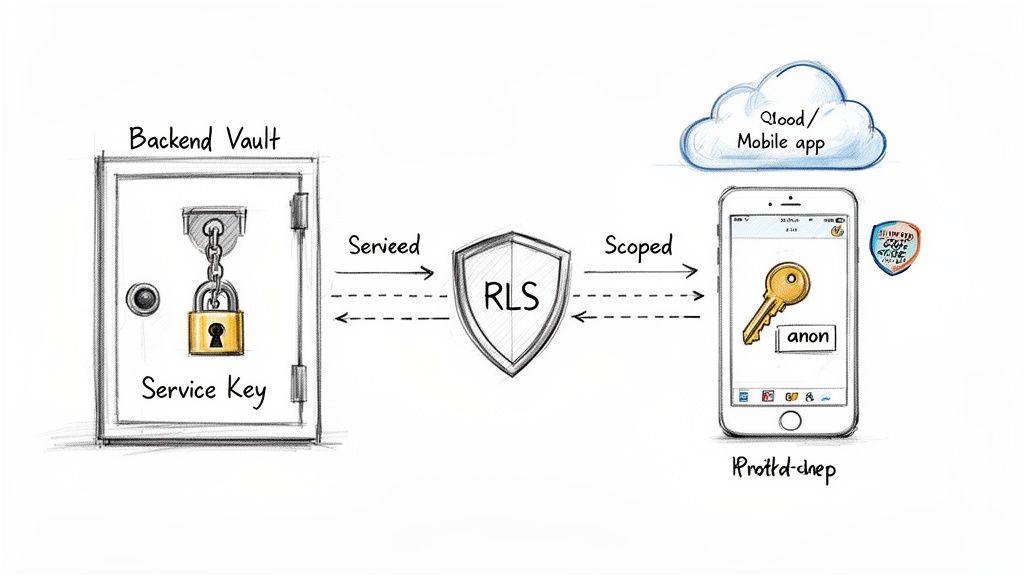
This strategy is central to the architecture of platforms like Supabase and Firebase. Client applications should only ever use the designated anon or public key. This key identifies your project but grants no inherent data access on its own. Instead, it relies on server-side rules, like PostgreSQL's Row Level Security (RLS) or Firebase's Security Rules, to determine what an authenticated or anonymous user is permitted to do. This model ensures that even if the public key is exposed, your data remains secure behind your authorisation layer, making it one of the most vital api security best practices to implement correctly.
Practical Implementation and Use Cases
The goal is to shift authorisation logic from the client to the backend, where it can be securely enforced. A public key acts as an entry ticket, but RLS acts as the bouncer, checking credentials for every single data request.
- To-Do List App: A mobile app uses Supabase's
anonkey. An RLS policy ensures that when a user queries thetodostable, they can only retrieve rows where theuser_idcolumn matches their own authenticatedauth.uid(). - SaaS Dashboard: A React application built on Firebase uses the public API key. Firebase Security Rules restrict access to a
/workspaces/{workspaceId}/datapath only to users whose authentication token includes a claim matching that{workspaceId}. - E-commerce Site: A public-facing storefront uses the
anonkey to display product listings, while RLS policies prevent it from accessing sensitive customer order data, which is only accessible after a user authenticates.
Actionable Tips for Hardening Key Management
Simply using public keys isn't enough; they must be paired with diligent security practices.
- Scan for Hardcoded Secrets: Regularly use tools like AuditYour.App to scan mobile app bundles (IPAs/APKs) and frontend code repositories for accidentally committed service keys or other secrets.
- Never Trust the Client: Always operate under the assumption that any key in a client-side application is public knowledge. Design your RLS and security rules to be robust enough to handle requests from un-trusted environments.
- Automate Secret Detection: Integrate secret scanning tools into your CI/CD pipeline. Use pre-commit hooks and services like GitHub's secret scanning to block commits containing sensitive keys.
- Rotate Keys Immediately: If a service-level key is ever compromised, revoke it immediately, generate a new one, and update your secure backend services. Monitor audit logs for any unusual activity.
For a comprehensive checklist on securing your API keys, review these guidelines on effective API key management, which cover prevention, detection, and response strategies.
3. Secure Remote Procedure Calls (RPCs) and Edge Functions
Remote Procedure Calls (RPCs), known as database functions in Supabase or Cloud Functions in Firebase, are server-side endpoints that encapsulate critical business logic. They often access privileged data and interact with third-party services, making them a high-value target for attackers. Securing these functions is a non-negotiable aspect of api security best practices, as a single vulnerable endpoint can compromise your entire system.
The core principle is to treat every function as a distinct, untrusted entry point to your application. This means each RPC must independently verify the caller's identity, validate all incoming data, and operate under the principle of least privilege. Neglecting this can lead to severe vulnerabilities, such as unauthorised data access, financial fraud, or system-wide denial of service.
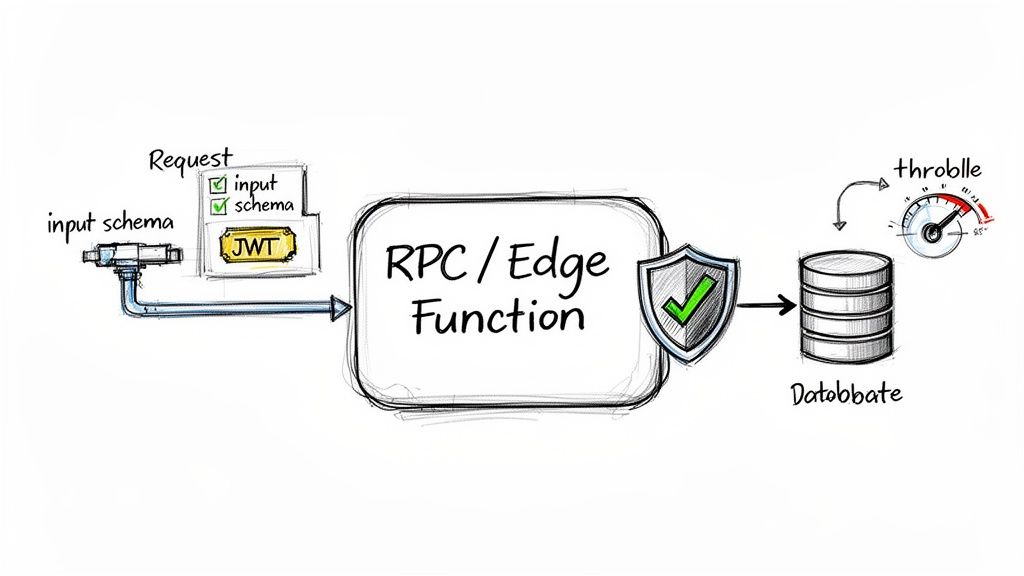
Practical Implementation and Use Cases
A robust security posture for RPCs involves layering multiple defence mechanisms. For instance, a payment processing function must not only check if a user is authenticated but also rate-limit requests to prevent attackers from repeatedly charging a customer's card.
- Admin Functions: An RPC that retrieves user data must check for a specific admin role within the user's JWT claims, not just their authentication status.
- Data Export Logic: A function that generates a user data export should enforce strict pagination and never return an entire dataset in one call to prevent data exfiltration.
- Password Resets: Ensure the function uses cryptographically secure, single-use tokens and validates them before allowing a password change.
Actionable Tips for Hardening RPCs
To effectively secure your backend functions, move beyond basic authentication and implement a comprehensive security checklist.
- Validate and Sanitise All Inputs: Use strict schemas to validate every parameter passed to your function. For RPCs interacting with a database, always use parameterised queries to completely eliminate the risk of SQL injection.
- Enforce Authorisation at the Entry Point: The very first step in any function should be to verify the caller's identity and permissions, typically by inspecting
auth.uid()or JWT claims. Deny the request immediately if authorisation fails. - Implement Strict Rate Limiting: Protect sensitive or resource-intensive functions from abuse. Apply a global limit (e.g., 100 calls/hour per user) and much stricter limits for operations like payment processing or account deletion.
- Use Dedicated, Low-Privilege Roles: Configure your RPCs to run with dedicated database roles that have the minimum permissions necessary to perform their task. For example, a function that only reads from a
profilestable should not have write access.
4. Implement Proper Authentication and Session Management
Authentication is the process of verifying a user's identity, forming the primary gateway to your API. Proper implementation involves more than just a username and password; it requires a robust strategy for handling session tokens like JWTs, managing their lifecycle, and defending against common attacks. This is a foundational pillar of modern api security best practices, as a compromised authentication system renders all other security measures useless.
The goal is to leverage established, battle-tested solutions instead of inventing a custom authentication mechanism, a notoriously error-prone endeavour. By default, you should use well-vetted providers like Supabase Auth or Firebase Authentication, which handle complex flows such as OAuth 2.0, magic links, and multi-factor authentication (MFA) securely out of the box. This strategy offloads immense security responsibility and helps prevent vulnerabilities like session hijacking and credential stuffing.
Practical Implementation and Use Cases
A correctly configured authentication system ensures that only legitimate users can access protected endpoints. It manages the entire user session, from initial sign-in to secure sign-out and token revocation.
- Social Logins: Integrating OAuth 2.0 providers like Google or GitHub simplifies user onboarding while delegating the complexities of password management to a trusted third party.
- Passwordless Flows: Using magic links or one-time passcodes (OTPs) sent via email or SMS provides a frictionless yet secure login experience, particularly for mobile applications.
- High-Security Operations: Requiring MFA before a user can perform sensitive actions, such as changing their email address or deleting their account, adds a critical layer of defence against account takeover.
Actionable Tips for Hardening Authentication
To secure your authentication and session management processes, focus on the token lifecycle and attack vector mitigation.
- Configure Short-Lived Tokens: Set JWT access token expirations to a short duration (e.g., 15-60 minutes) and use long-lived refresh tokens (7-30 days) to obtain new access tokens.
- Secure Token Storage: For web applications, store tokens in
HttpOnly,Securecookies to prevent access via JavaScript (XSS). For mobile apps, use the platform's secure storage, like Keychain on iOS or Keystore on Android. - Implement Secure Logout: Ensure your logout function properly invalidates the session on the server-side by revoking the associated refresh token, rather than just deleting the token on the client.
- Test Authentication Flows: Rigorously test your implementation by checking for vulnerabilities like improper handling of expired tokens, weak signature validation, and insecure password reset mechanisms.
5. Validate and Sanitize All Input Data
Treating all client-side input as inherently untrusted is a foundational principle of secure API development. Input validation and sanitisation involve rigorously checking every piece of data received by your API to ensure it conforms to expected formats, types, and constraints before it is processed or stored. This defensive strategy is a critical layer in your api security best practices, acting as the first line of defence against a wide range of injection attacks and business logic abuse.
By default, any data coming from a web browser, mobile app, or third-party service can be manipulated. The core idea is to enforce a strict "allow-list" approach, where you define exactly what is acceptable and reject everything else. This proactive validation, applied at multiple layers (client, API gateway, and application backend), prevents malicious payloads from ever reaching your core business logic or database, effectively neutralising threats like SQL injection and Cross-Site Scripting (XSS).
Practical Implementation and Use Cases
A common scenario involves a user registration form. Input validation would ensure the email is a valid format, the password meets complexity requirements, and the username is within a specific length and character set. Sanitisation would then escape any special characters to prevent them from being misinterpreted by the database or browser.
- E-commerce Platforms: Validate product quantities to ensure they are positive integers and check discount codes against a list of valid, active codes to prevent logic abuse.
- Social Media Apps: Sanitize user-generated comments by escaping HTML characters to block XSS attacks, preventing one user from injecting malicious scripts into another's browser.
- Backend Services: When accepting file uploads, validate the file type (e.g., only
image/jpeg), size, and scan it for malware before saving it to storage.
Actionable Tips for Hardening Input Validation
Effective validation requires a systematic and layered approach that goes beyond simple front-end checks.
- Use Schema Validation Libraries: Employ robust libraries like Zod or Joi to define and enforce strict schemas for your API request bodies, ensuring data structure and types are correct.
- Never Concatenate User Input into Queries: Always use parameterised queries or prepared statements provided by your database driver. This is the single most effective way to prevent SQL injection.
- Log All Validation Failures: Send validation failure events to your logging system. This provides crucial visibility into potential attack attempts and helps in security monitoring and threat analysis.
- Test with Malicious Payloads: Actively test your endpoints with common attack payloads (e.g.,
' OR '1'='1',<script>alert('XSS')</script>,../) to confirm your validation logic correctly rejects them.
6. Implement Rate Limiting and DDoS Protection
Rate limiting is a critical defence mechanism that controls the frequency of API requests a user or IP address can make within a specific time frame. By setting thresholds, you can effectively mitigate automated threats like brute-force login attempts, credential stuffing, and Denial-of-Service (DoS) attacks that aim to overwhelm your backend resources. This practice is an essential component of modern api security best practices, ensuring both the availability and integrity of your services.
The core principle is to prevent abuse before it impacts your system. Unchecked API access allows malicious actors to bombard your application, leading to performance degradation or complete service outages. Implementing sensible limits at multiple layers, from your infrastructure and API gateway down to individual application endpoints, creates a robust defence against both targeted attacks and unintentional resource exhaustion from buggy client applications.
Practical Implementation and Use Cases
Effective rate limiting involves creating nuanced policies tailored to specific endpoints and user states. For instance, a login endpoint requires much stricter limits than a public, read-only data endpoint.
- Authentication Endpoints: Limit login attempts to 5 per IP address per minute to thwart brute-force attacks. Similarly, restrict password reset requests to 3 per email address per hour to prevent abuse.
- Resource-Intensive Operations: Control file uploads to a certain size or number per hour (e.g., 10MB per user per hour) to prevent storage abuse.
- API Tiers: For public APIs, enforce usage quotas like 1,000 requests per API key per day for a free tier, protecting your service from overuse.
Actionable Tips for Hardening Rate Limiting
To implement a comprehensive rate limiting strategy, consider the following technical approaches.
- Leverage Platform Capabilities: Use the built-in rate limiting features of your API gateway or platform, such as Vercel Edge Middleware or Supabase's provided configurations.
- Differentiate User Types: Apply stricter limits to unauthenticated or anonymous users compared to authenticated, trusted users.
- Provide Clear Client Feedback: When a limit is exceeded, return an HTTP 429 (Too Many Requests) status code along with a
Retry-Afterheader to guide well-behaved clients on when to try again. - Monitor and Adapt: Actively monitor your rate limit metrics to identify emerging attack patterns or legitimate use cases that require adjusted thresholds.
- Configure DDoS Protection: For large-scale volumetric attacks, rely on a dedicated DDoS protection service at the CDN or network edge, such as Cloudflare or Vercel's integrated solutions.
7. Secure API Communication with HTTPS and Encryption
Encrypting data both in transit and at rest is a non-negotiable layer of defence in modern application development. All communication between your client application (web or mobile) and your backend API must be forced over HTTPS (Hypertext Transfer Protocol Secure), which uses TLS (Transport Layer Security) to create a secure, encrypted channel. This practice is a fundamental component of api security best practices, preventing attackers from intercepting and reading sensitive data like credentials, tokens, or personal information as it travels across networks.
Platforms like Supabase and Firebase enforce HTTPS for all API interactions by default, providing a strong baseline. However, a comprehensive strategy also includes encrypting sensitive data at rest, meaning the data is unreadable even if an attacker gains direct access to the database storage. This dual-layered approach ensures data is protected from both network snooping and physical storage breaches.
Practical Implementation and Use Cases
Securing data in transit and at rest is a universal requirement for any application handling sensitive information. The goal is to protect data integrity and confidentiality at every stage of its lifecycle.
- Financial Applications: An HSTS (HTTP Strict Transport Security) header prevents downgrade attacks, ensuring a user's browser only ever communicates with the banking app's API over a secure HTTPS connection.
- Mobile Apps: Implementing certificate pinning prevents man-in-the-middle (MITM) attacks where an attacker uses a rogue certificate to intercept and decrypt API traffic from a mobile device on a public Wi-Fi network.
- Healthcare Platforms: Encrypting specific database columns containing Patient Health Information (PHI) at rest adds a crucial layer of compliance and security, protecting data even if the underlying database is compromised.
Actionable Tips for Hardening Encryption
Beyond just enabling HTTPS, robust security requires diligent configuration and ongoing maintenance.
- Enforce Strong TLS and HSTS: Configure your server to use modern TLS versions (1.2+) and disable weak, outdated cipher suites. Implement the HSTS header to instruct browsers to exclusively use HTTPS.
- Implement Certificate Pinning for Mobile Apps: For high-security mobile applications, pin the server's public key or certificate within the app. This ensures the app only trusts your specific server, thwarting most MITM attacks.
- Automate Certificate Management: Use services like Let's Encrypt to automate the renewal of SSL/TLS certificates, keeping their validity period short (e.g., 30-90 days) to limit the window of exposure if a key is ever compromised.
- Test Your Configuration: Regularly use tools like SSL Labs to analyse your server's TLS configuration. This helps identify weak ciphers, protocol vulnerabilities, and certificate chain issues that could weaken your security posture.
8. Implement Comprehensive Audit Logging and Monitoring
Effective API security extends beyond prevention; it requires robust detection and response capabilities. Comprehensive audit logging creates a detailed, immutable record of all significant events within your system, capturing who did what, when, and from where. This practice is a cornerstone of modern api security best practices, enabling you to detect anomalies, investigate incidents, and meet compliance obligations.
Without diligent logging and monitoring, your application is effectively a black box. You cannot identify a brute-force attack in progress, spot an insider threat accessing unusual data, or trace the steps of an attacker after a breach. Platforms like Supabase and Firebase provide built-in logging capabilities (e.g., Supabase Audit Logs, Firebase Cloud Logging) that serve as a crucial foundation for this security layer.

Practical Implementation and Use Cases
A well-implemented logging strategy is your primary tool for incident response and threat hunting. By centralising and analysing logs, you can transform raw data into actionable security intelligence.
- Threat Detection: Identify a brute-force attack by alerting on a high volume of failed login attempts from a single IP address within a short timeframe.
- Insider Threat Identification: Discover potential misuse by monitoring for unusual data access patterns, such as a support agent accessing high-profile customer records outside of a support ticket context.
- Compliance and Forensics: Use detailed access logs to prove compliance with standards like GDPR or HIPAA and to reconstruct the timeline of a security incident for post-mortem analysis.
- Compromised Key Detection: Spot a stolen API key being used from an unexpected geographical location by setting up location-based anomaly detection alerts.
Actionable Tips for Hardening Logging and Monitoring
Merely enabling logging is not enough; the quality and security of the logs are paramount.
- Log All Critical Events: Record every API call, including the authenticated user ID, endpoint, HTTP method, response status, timestamp, and source IP address. For authorisation failures, log what the user tried to access and why it was denied.
- Use Structured Logging: Employ a consistent format like JSON. Structured logs are far easier for automated systems (like a SIEM) to parse, query, and generate alerts from compared to plain text.
- Sanitise Sensitive Data: Never log plaintext passwords, full credit card numbers, or other highly sensitive personal information. This prevents your logs from becoming a security liability themselves.
- Configure Proactive Alerts: Set up automated alerts for suspicious patterns, such as more than five failed logins from one IP in five minutes, a sudden spike in API errors, or access attempts on disabled accounts.
- Ensure Log Immutability and Retention: Store logs in a secure, centralised, and tamper-proof location. Retain logs for a minimum of 90 days, or longer if required by compliance standards like PCI-DSS.
9. Follow API Versioning and Deprecation Practices
API versioning is the practice of managing changes to your API in a way that prevents breaking changes for client applications. By segmenting your API into versions (e.g., /api/v1/, /api/v2/), you can introduce new features, modify data structures, and patch vulnerabilities without disrupting existing users. This is a critical component of long-term api security best practices, as it provides a structured pathway to deprecate and remove insecure or outdated endpoints.
A disciplined versioning strategy allows you to evolve your backend's security posture over time. The core principle is to start with versioning from day one, even if it's just /v1/. This avoids the difficult migration from an unversioned default API. A clear lifecycle for each version, including a well-communicated deprecation schedule, ensures that security fixes that require breaking changes can be rolled out responsibly and predictably.
Practical Implementation and Use Cases
A common scenario is discovering a security flaw in an early API design that requires a fundamental change. For example, an old password reset endpoint might be vulnerable to enumeration attacks. Instead of patching it in a way that breaks existing mobile apps, you would introduce a new, secure token-based flow in /v2/ and announce the deprecation of the /v1/ endpoint.
- Upgrading Authorisation Logic: A breaking change in v2 could enforce stricter RLS policies that prevent data bypasses possible in v1.
- Removing Insecure Endpoints: Sunset an old endpoint that transmitted unencrypted data after providing a 12-month notice and a secure v2 alternative.
- Adopting New Standards: Move from a simple API key to a more secure OAuth 2.0 flow in a new major version, giving developers time to migrate.
Actionable Tips for Hardening Versioning
Effective versioning is more than just adding a number to your URL; it requires a clear process.
- Communicate Clearly: Use deprecation headers (
Deprecation: true,Sunset: [date]) and maintain a public changelog detailing breaking changes and migration guides. - Monitor Usage: Log which API versions are actively being used. This data is invaluable for identifying which clients need to be notified before a version is retired.
- Backport Critical Security Patches: If possible, backport high-severity security fixes to older but still-supported major versions to protect users who haven't migrated yet.
- Automate Version Testing: Ensure your CI/CD pipeline runs security and regression tests against all supported API versions, not just the latest one.
10. Implement Automated Security Testing in CI/CD Pipelines
Integrating security scanning directly into your Continuous Integration/Continuous Deployment (CI/CD) pipeline transforms security from an afterthought into an automated, proactive process. This DevSecOps practice involves embedding various security checks that run automatically whenever code is committed or a new build is deployed. This is a crucial element of modern api security best practices, as it catches vulnerabilities before they ever reach production.
The core principle is to shift security left, identifying and remediating issues early in the development lifecycle when they are cheapest and easiest to fix. By automating scans for secrets, vulnerable dependencies, and misconfigurations, you create a security gate that prevents common risks from being deployed. This prevents security debt from accumulating and hardens your application's posture with every commit.
Practical Implementation and Use Cases
Automated security can take many forms within a typical development workflow, providing layers of protection from code creation to deployment.
- Dependency Scanning: A tool like
npm auditor Dependabot automatically scans your project's dependencies and can be configured to fail the build if a high-severity vulnerability is found. - Static Application Security Testing (SAST): GitHub Advanced Security or GitLab SAST can scan code before a pull request is merged, flagging potential issues like SQL injection or insecure function usage.
- Backend Configuration Scanning: Tools like AuditYour.App can be integrated into your deployment script to scan your Supabase or Firebase project for insecure RLS policies, exposed secrets, or misconfigured security rules on every deployment.
- Secret Scanning: Pre-commit hooks or pipeline jobs can prevent developers from accidentally committing API keys, database credentials, or other sensitive information into the version control history.
Actionable Tips for Hardening CI/CD Security
To make automated testing effective, it needs to be comprehensive and enforced.
- Fail Builds on Critical Findings: Configure your CI pipeline to block merges or deployments if critical or high-severity vulnerabilities are detected by any scanning tool.
- Use Pre-Commit Hooks: Implement local checks that run before code is even committed. This is an excellent first line of defence against committing secrets.
- Test RLS and Security Rules: Your CI process should include dedicated tests that verify your authorisation rules work as expected, preventing logic flaws that could lead to data leaks.
- Scan Infrastructure as Code (IaC): If you define your cloud infrastructure using tools like Terraform, use scanners to check for insecure configurations before they are applied.
For a detailed walkthrough on setting up these automated checks, review this comprehensive automated security scanning guide which covers tooling and best practices.
API Security Best Practices — 10-Point Comparison
| Item | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ | |---|---:|---:|---:|---|---| | Implement Row Level Security (RLS) with Proper Authorization Rules | High — policy design & testing required 🔄🔄🔄 | Moderate — DB support, testing frameworks, auth claims ⚡⚡ | Strong data isolation; prevents app-layer bypass 📊 ✅ | Multi-tenant SaaS, healthcare, fintech where per-user/org isolation is required 💡 | ⭐ Enforces data-layer access; reduces attack surface | | Protect API Keys and Use Public/Anon Keys with RLS | Medium–High — infra & process changes; dev discipline 🔄🔄 | High — secret vaults, CI/CD scanning, proxies, rotation ⚡⚡⚡ | Significantly lowers leaked-key risk; limits blast radius 📊 ✅ | Frontend/mobile apps, public clients where secrets could leak 💡 | ⭐ Cuts largest credential attack vector; enables centralized revocation | | Secure Remote Procedure Calls (RPCs) and Edge Functions | Medium — validation, auth checks, least-privilege 🔄🔄 | Moderate — secure function hosting, logging, rate limits ⚡⚡ | Centralized secure business logic; fewer client bypasses 📊 ✅ | Payment flows, admin actions, data exports, sensitive operations 💡 | ⭐ Central control for auth/validation; easier auditing | | Implement Proper Authentication and Session Management | Medium — token handling and refresh complexity 🔄🔄 | Moderate — auth provider or infrastructure, MFA, token storage ⚡⚡ | Reliable identity; enables correct authorization decisions 📊 ✅ | All apps requiring user identity: web, mobile, enterprise 💡 | ⭐ Strong identity foundation; reduces credential attacks | | Validate and Sanitize All Input Data | Low–Medium — consistent schema enforcement 🔄🔄 | Low — validation libraries, testing, dev discipline ⚡⚡ | Reduces injection/XSS and malformed requests; improves data quality 📊 ✅ | Any endpoint accepting user input; RPCs, forms, file uploads 💡 | ⭐ Prevents many injection classes; easy with modern libs | | Implement Rate Limiting and DDoS Protection | Medium — tuning and distributed state needed 🔄🔄 | High — gateways/CDN, Redis/state, monitoring ⚡⚡⚡ | Mitigates brute force, abuse, and service disruption 📊 ✅ | Login/password reset, public APIs, upload/search endpoints 💡 | ⭐ Protects availability; reduces abuse and costs | | Secure API Communication with HTTPS and Encryption | Low — standard server config but ongoing management 🔄 | Low–Moderate — certs, config, optional pinning ⚡⚡ | Protects data-in-transit; prevents MitM attacks 📊 ✅ | All networked applications; high-value data transfers 💡 | ⭐ Essential baseline; straightforward with modern tools | | Implement Comprehensive Audit Logging and Monitoring | Medium — log design, retention, SIEM integration 🔄🔄 | High — storage, aggregation, alerting, analysts ⚡⚡⚡ | Enables detection, forensics, and compliance evidence 📊 ✅ | Regulated environments, incident response readiness, large apps 💡 | ⭐ Critical for detection/response and compliance | | Follow API Versioning and Deprecation Practices | Low–Medium — policy and CI discipline 🔄🔄 | Low — routing/versioning, docs, monitoring ⚡⚡ | Enables safe API evolution and removal of vulnerable endpoints 📊 ✅ | Public APIs, long-lived clients, breaking security changes 💡 | ⭐ Reduces client breakage; allows secure deprecation | | Implement Automated Security Testing in CI/CD Pipelines | Medium — toolchain integration and maintenance 🔄🔄 | Moderate — scanners (SAST/DAST), compute, config ⚡⚡⚡ | Finds issues pre-release; reduces security debt and risk 📊 ✅ | All projects aiming for DevSecOps and frequent releases 💡 | ⭐ Early detection; enforces security gates in deploys |
From Checklist to Culture: Making API Security Continuous
We have journeyed through the ten foundational pillars of modern API security, moving from the granular control of Row Level Security to the broad oversight of automated CI/CD pipelines. This exploration of API security best practices is more than just a technical checklist; it is a strategic blueprint for building resilient, trustworthy applications, especially within dynamic ecosystems like Supabase and Firebase. Each practice, whether it’s diligently protecting your API keys, sanitising every input, or securely architecting your RPCs and Edge Functions, contributes to a multi-layered defence. Ignoring even one can leave a critical gap for attackers to exploit.
The core message is a fundamental shift in mindset. Security is not a feature you add at the end of a development cycle or a box you tick before deployment. It is an ongoing discipline, a cultural commitment that must be woven into every stage of your product's lifecycle. The transition from a static, point-in-time security audit to a continuous, automated process is no longer a luxury for large enterprises; it is a necessity for startups and indie developers who need to move quickly without compromising user trust.
Synthesising the Blueprint for Secure Development
Let's distill the most critical takeaways from our discussion. The journey towards robust API security begins with a "secure by default" posture, and for platforms like Supabase, this is epitomised by Row Level Security (RLS).
- Authentication and Authorisation as the Bedrock: Strong authentication confirms who a user is, but robust authorisation, primarily through RLS and function-level checks, dictates what they are allowed to do. These two elements are inseparable and form the absolute foundation of your security model.
- The Perimeter Has Shifted: In a world of serverless functions and direct-to-database client access, your security perimeter is not a distant firewall but is defined by the logic within each API endpoint and database policy. Every RPC, every table, and every function is a potential entry point that must be independently secured.
- Automation is Your Greatest Ally: The complexity of modern applications and the rapid pace of development make manual security checks impractical and prone to error. Integrating automated scanning into your CI/CD pipeline transforms security from a bottleneck into a seamless, proactive part of your workflow. This allows you to catch misconfigurations and regressions before they ever reach production.
Mastering these concepts means you are not just preventing breaches; you are building a competitive advantage. Users gravitate towards products they can trust, and a strong security posture is a powerful signal of quality and reliability. It allows you to innovate with confidence, knowing your core infrastructure is sound.
Your Actionable Path Forward
Moving from theory to practice is the most crucial step. Start by assessing your current state. Where are the most significant gaps in your implementation of these API security best practices? Begin with the highest-impact areas. If you haven't fully implemented RLS, make that your immediate priority. If your API secrets are hardcoded, address that vulnerability today.
Next, establish a baseline. A comprehensive security scan can provide an immediate, objective view of your current security health, highlighting vulnerabilities you may have overlooked. This initial snapshot is your starting point for iterative improvement. From there, the goal is to embed this process directly into your development workflow. By making security validation an automated step in every pull request, you empower your developers to own security, fix issues as they arise, and maintain a high standard of protection continuously. This cultural shift, powered by the right tools, is what ultimately separates fragile applications from truly resilient ones.
Ready to move beyond the checklist and embrace continuous security? Get an instant, comprehensive security baseline for your Supabase project with AuditYour.App. Our automated platform scans for the very misconfigurations and vulnerabilities discussed in this article, giving you a clear, actionable report in minutes. Start your journey to a stronger security posture today at AuditYour.App.
Scan your app for this vulnerability
AuditYourApp automatically detects security misconfigurations in Supabase and Firebase projects. Get actionable remediation in minutes.
Run Free Scan